Investigate Two
Introductions
How you as an analyst handle true positives is life and death in the eyes of potential victims. Traditionally the industry elected to prioritize overzealousness and sending more than not to cover their failings, This however is no different to guesses and it is possible to arrive at strong data-backed decisions on events that could be the compromise of an estate
True Positive
True positives exist at the heart of all our jobs, they are what we wake up for in the
morning and why we endlessly pursue understanding how to protect our clients. The
strictest possible definition of true positive is where an outcome of a prediction or model
is returned true. This broad definition is important because the assumption carried with
a predication or model can change. As an example many security technologies aim to
identify when an application often unwanted by an organization is present within a
system, these are commonly dubbed PUPs. (Potentially Unwanted Programs).
morning and why we endlessly pursue understanding how to protect our clients. The
strictest possible definition of true positive is where an outcome of a prediction or model
is returned true. This broad definition is important because the assumption carried with
a predication or model can change. As an example many security technologies aim to
identify when an application often unwanted by an organization is present within a
system, these are commonly dubbed PUPs. (Potentially Unwanted Programs).
The general consensus is that PUPs do not bring an immediate threat to an
organization however when you traditionally compare the qualities of a PUP vs another
file, qualities of that PUP will be more suggestive of an opportunity to be abused. As
such when security technologies identify PUPs they are considered True Positives.
organization however when you traditionally compare the qualities of a PUP vs another
file, qualities of that PUP will be more suggestive of an opportunity to be abused. As
such when security technologies identify PUPs they are considered True Positives.
Considering other models or projections abstracted by detections is important when
establishing the criticality of your investigation and where on the spectrum of criticality
you land. Another common example is the deletion of shadow volumes. Often alerts
derived from detections looking for Shadow Volume copies being enumerated and
removed will label themselves “Ransomware Activity”.
establishing the criticality of your investigation and where on the spectrum of criticality
you land. Another common example is the deletion of shadow volumes. Often alerts
derived from detections looking for Shadow Volume copies being enumerated and
removed will label themselves “Ransomware Activity”.
Now on your own review of these alerts you may find that a shadow volume copy was
removed but it was a necessary step in an organization’s backup process. So from the
perspective of the model or prediction it successfully raised a true positive however from
analysts’ perspective, it was a false positive because an analyst’s own model or
prediction will always be “Was this an adversary”
removed but it was a necessary step in an organization’s backup process. So from the
perspective of the model or prediction it successfully raised a true positive however from
analysts’ perspective, it was a false positive because an analyst’s own model or
prediction will always be “Was this an adversary”
This mindset is critical because you may look at numerous true positives a day and of
course even more false positives, but it is expected of an analyst to know out of the
noise which true positive needs escalating into greater human eyes or simply forward to
a client as a polite reminder.
course even more false positives, but it is expected of an analyst to know out of the
noise which true positive needs escalating into greater human eyes or simply forward to
a client as a polite reminder.
Ugly True Positives
Now that we have explored how different true positives can exist I have coined the term
“Ugly True positive’ to denote those that must initiate major incident response
procedures when found. Ugly true positives are measured by how much impact the next
possible action could cause. As an example (colours will darken as the more ugly the investigation leads)
“Ugly True positive’ to denote those that must initiate major incident response
procedures when found. Ugly true positives are measured by how much impact the next
possible action could cause. As an example (colours will darken as the more ugly the investigation leads)
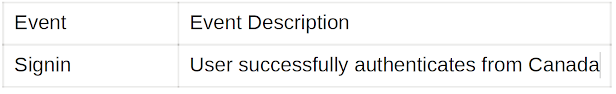
Immediately with the information we have in the table we will want to establish whether
authentication attempts from Canada normally occur.
While asking these investigative questions we can already start thinking about if this
was an event generated by an adversary they would now have access to the data the account does
We now have more information and can ask our self “What data specifically would an
adversary have access to within Exchange Online”
Exchange online can have huge scope and what people can access is largely
dependant on ACLs configured within the app and unfortunately not something present
in our events,
We can now view what activity occurred within the app exchange online after the
date./time of the authentication request
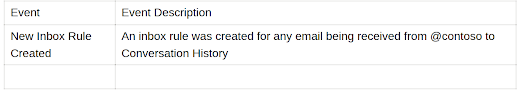
After the successful authentication, the same user established an inbox rule to forward
emails from the domain “@contoso” to Conversation History. We know the location of
Conversation History within a mailbox is scarcely used let only for an inbox rule.
Adversaries are well known to perform this technique to allow themselves and the victim
to persist in the mailbox at the same time
Now what we are investigating is starting to get ugly, at first, we had a true positive but
on its own it meant nothing to us and now we are seeing activity occur that we wouldn’t
expect a human to do.’ At this point, you want to increase the amount of energy we are
expending because we have moved to post-compromise activity which is the ugliest of
all.
on its own it meant nothing to us and now we are seeing activity occur that we wouldn’t
expect a human to do.’ At this point, you want to increase the amount of energy we are
expending because we have moved to post-compromise activity which is the ugliest of
all.
An analysts nightmare
Below are some tell tall signs you have found an ugly true positive:
- Identification of initial access followed by escalating activity
- Recurrence of the same alert across multiple assets
- Unrelated alerts converging on a common objective
Analyst Response
Once you have understood the type of true positive and the concept of “what is the
worst that could happen next” to establish how critical the true positive is you now need
to decide how you are going to respond. At minimum, for all true positives, you must
- Document its discovery and your classification
- Detail your investigative steps
- Inform the local team
- What actions you would like to take further
However, if you are presented with or have discovered an ugly true positive
- Escalate to team leadership
- Articulate the severity and the data you used.
- Prepare for containment and post-compromise assessment
Once immediate actions are completed as an analyst you will want to switch tracks towards" How can we learn from this", "what role did our controls place in this and did they behave expectedly". You as the analyst need to take ownership of your findings and conclusions and declare what you investigate malicious or a false positive. Do not attempt to pass it along let it slide as a notification of something suspicious
Engineering the Ugly True Positives
If you build detections and engineer how those detections exist within a lifecycle you
need to be measuring how severe a situation it is if the detection fires. Using context a
detection should behave in different ways.
need to be measuring how severe a situation it is if the detection fires. Using context a
detection should behave in different ways.
Some detections should skip 200 and go straight to jail alerting and ultimately executing
major incident response procedures immediately for example when 200 of the largest
EC2 instance plans are span up in under an hour. But some detections need to serve as
little pieces to a puzzle like “connections made on high-ranged ports for new binaries”
being joined to “new binary spawning script interpreter” and as these little puzzle pieces
build up to a threshold that is established and if lapsed you have your self an Ugly true
positive.
How the detections manifest to analysts can go a long way too, the words High
Severity and the Colour Red doesn’t really carry any conscious weight in the mind
when asking investigative questions. So explicitly detail what an adversary could
achieve if the activity is a true positive, what data is at risk and include tips, tricks and
pivot points to get to more pertinent data faster
In addition, if as an engineer you have devised logic that has a high certainty of a trigger
being a True Postive, review the analysts own processes for such an occasion and see
if you can alleviate each step. In particular, if you know that after a business email
compromise-related detection analysts will want to receive all the FileDownload
OfficeActivity operations have those results immediately ready in the alert.
Furthermore, dedicate time to thoroughly investigate your detections and formulate qualitative benchmarks to enhance their reliability. This preparation will empower you to incorporate switch response and containment measures when confronted with "ugly true positives" all without requiring manual intervention
Presentation to analysts in an art, with clarity trumping generic severity labels. Envisioning an adversary's potential exploits and offering strategic pivots to facilitate an efficient investigation. Tailing detections to analyst workflow streamlines their process. enabling rapid action. the fusion of distinct detections amplifies their collective impact and constructs timelines for comprehensive analysis
You could summarize the role of an engineer during an active investigation as bringing the lead > causality time down to as short as possible.
Summary
When performing an investigation and you arrive to a decision point think about what
the impact of the events could mean, think about the abnormality of it. how would the
activity give an adversary an advantage and is it an already known procedure?